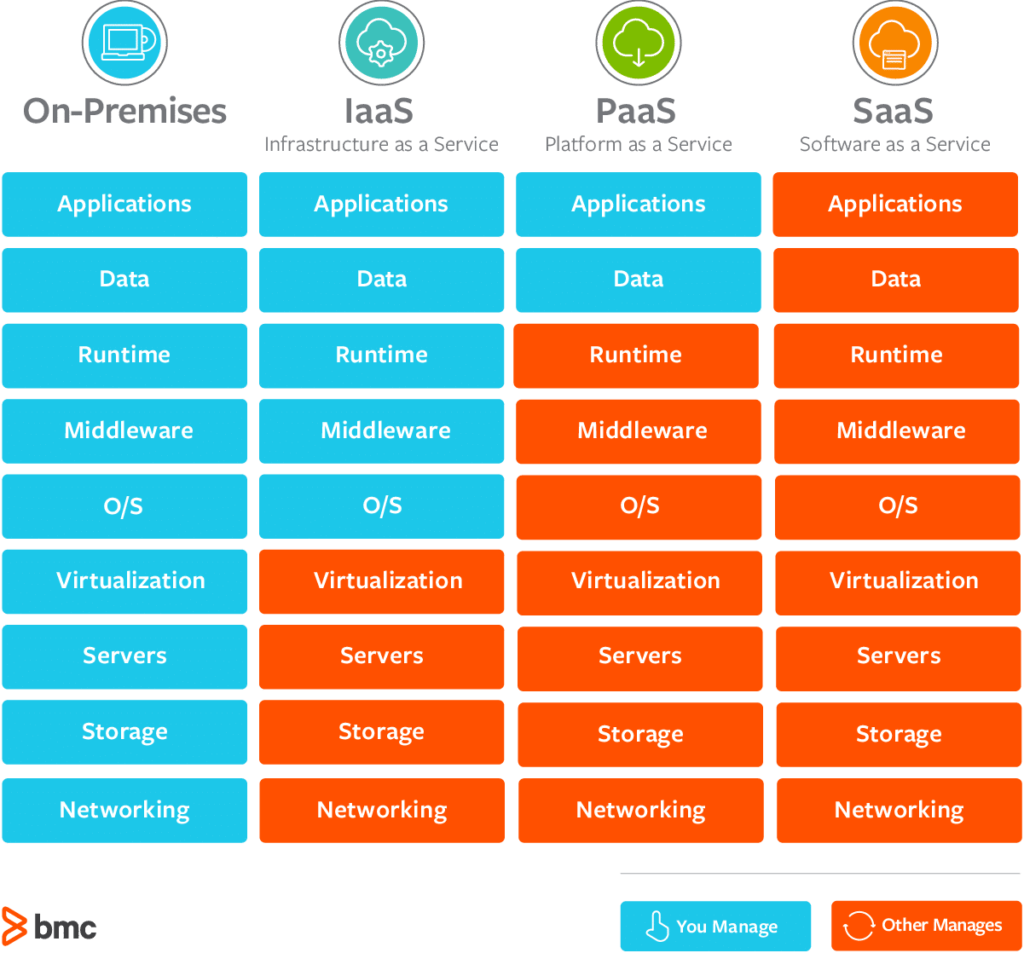
Cloud Services - Specialist Solutions for Modern Services
Cloud Services - Specialist Solutions for Modern Services
Blog Article
Utilize Cloud Provider for Improved Information Security
Leveraging cloud services offers a compelling service for organizations looking for to fortify their data protection procedures. The question arises: how can the use of cloud services reinvent information protection practices and provide a robust shield against potential susceptabilities?
Relevance of Cloud Security
Making certain durable cloud protection measures is vital in protecting sensitive data in today's electronic landscape. As companies progressively rely upon cloud solutions to store and process their data, the need for strong protection methods can not be overemphasized. A breach in cloud protection can have extreme consequences, ranging from monetary losses to reputational damages.
One of the primary reasons cloud safety and security is essential is the shared responsibility design used by most cloud company. While the company is liable for protecting the facilities, clients are in charge of protecting their data within the cloud. This division of duties underscores the value of carrying out robust protection actions at the customer degree.
Moreover, with the expansion of cyber threats targeting cloud environments, such as ransomware and information breaches, organizations must stay proactive and attentive in mitigating threats. This entails consistently upgrading safety and security protocols, checking for dubious activities, and informing employees on best methods for cloud security. By focusing on cloud protection, organizations can better shield their sensitive information and maintain the depend on of their stakeholders and customers.
Information Encryption in the Cloud
File encryption in the cloud generally involves using cryptographic algorithms to scramble information right into unreadable layouts. This encrypted data can only be figured out with the matching decryption trick, which adds an added layer of safety and security. Furthermore, numerous cloud provider offer encryption systems to safeguard information at remainder and en route, boosting general information security. Implementing durable encryption techniques along with various other safety actions can substantially boost a company's defense versus cyber hazards and protect important details stored in the cloud.
Secure Information Back-up Solutions
Information backup options play an important role in making sure the strength and safety and security of information in the occasion of unforeseen cases or data loss. Safe and secure information backup solutions are crucial parts of a durable data protection strategy. By frequently backing up data to protect cloud servers, organizations can reduce the risks related to data loss as a result of cyber-attacks, equipment failings, or human mistake.
Applying safe and secure information backup services includes picking trusted cloud service companies that provide encryption, redundancy, and data honesty procedures. Additionally, data stability checks ensure that the backed-up information continues to be unaltered and tamper-proof.
Organizations ought to develop computerized backup schedules to ensure that information is consistently and successfully backed up without hands-on treatment. Routine screening of data repair processes is additionally essential to assure the efficiency of the backup options in recouping information when required. By spending in protected information backup services, services can boost their data protection stance and reduce the impact of possible information violations or disruptions.
Role of Gain Access To Controls
Applying rigid accessibility controls is critical for keeping the security and integrity of delicate info within business systems. Access controls function as an essential layer of defense versus unapproved access, making sure that only accredited like this individuals can check out or adjust sensitive information. By defining who can access particular sources, companies can restrict the threat of data violations and unauthorized disclosures.
Regularly examining and upgrading access controls is vital to adapt to organizational adjustments and progressing safety and security risks. Continual monitoring and auditing of gain access to logs can aid identify any dubious tasks and unapproved gain access to efforts quickly. Overall, durable access controls are essential in guarding delicate information and mitigating safety and security threats within organizational systems.
Conformity and Rules
Frequently making sure conformity with pertinent policies and requirements is important for companies to promote data protection and privacy measures. In the realm of cloud services, where information is typically saved and refined externally, adherence to industry-specific regulations such as GDPR, HIPAA, or PCI DSS is essential. universal cloud Service.
Cloud solution companies play a crucial function in assisting organizations with compliance initiatives by offering services and features that align with various regulatory needs. As an example, numerous service providers supply encryption capabilities, access controls, and audit trails to help organizations meet information security criteria. In addition, some cloud services go through routine third-party audits and accreditations to demonstrate their adherence to market laws, providing added guarantee to companies looking for compliant solutions. By leveraging compliant cloud solutions, organizations can improve their information protection position while fulfilling regulative obligations.
Verdict
In conclusion, leveraging cloud solutions for boosted information safety and security is crucial for companies to check out here protect delicate details from unapproved access and possible breaches. By carrying out durable cloud safety procedures, consisting of information security, safe and secure backup options, access controls, and conformity with policies, businesses can benefit from sophisticated security actions and proficiency supplied by cloud provider. This assists mitigate threats successfully and guarantees the privacy, honesty, and availability of information.
Information back-up remedies play a critical role in ensuring the durability and safety and security of data in the event of unforeseen occurrences or data loss. By regularly backing up information to protect cloud servers, companies can reduce the risks associated with data loss due to cyber-attacks, equipment failings, or useful link human mistake.
Implementing safe and secure information backup services entails selecting trustworthy cloud service carriers that supply file encryption, redundancy, and data integrity measures. By investing in protected data backup services, companies can improve their data safety and security posture and decrease the influence of prospective information violations or disturbances.
Report this page